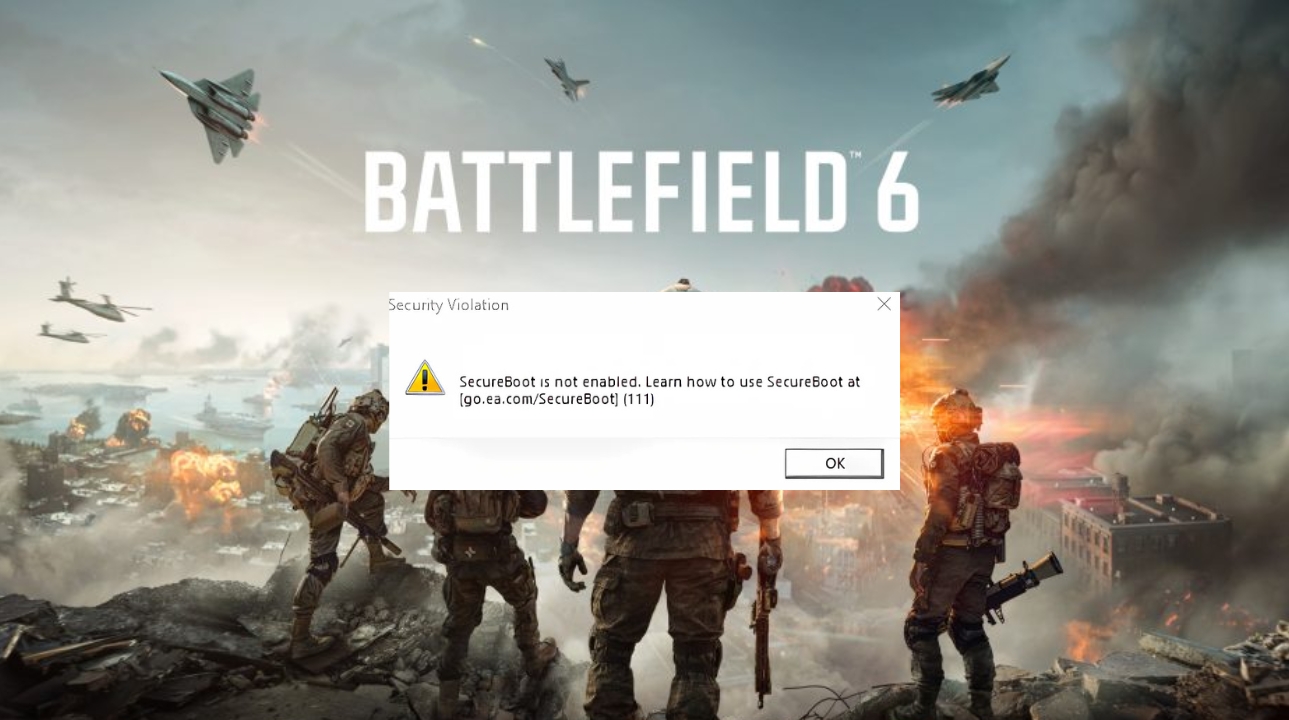
**What’s Driving the Surge in Interest Around Secure Boot Battlefield 6?** As digital devices grow more integral to daily life and enterprise operations, securely booting and protecting systems from unauthorized access has become a top priority. Among the most discussed developments is Secure Boot Battlefield 6—an advanced security protocol gaining momentum across the U.S. market. With rising concerns over device compromise, supply chain integrity, and endpoint resilience, this next-generation secure boot framework is shifting how users think about trust in hardware and software ecosystems. Profile searches for Secure Boot Battlefield 6 reflect growing awareness of secure startup processes and their role in fortifying digital infrastructure. **Why Secure Boot Battlefield 6 Is Reshaping Digital Security Discussions** In an era where cyber threats evolve rapidly, Many companies and tech-savvy individuals are seeking robust solutions to ensure their systems boot only verified, trusted code. Secure Boot Battlefield 6 responds to this need by integrating enhanced cryptographic measures, firmware validation, and tamper-resistant boot sequences. Its emergence aligns with broader industry efforts to counter sophisticated attacks, perimeter breaches, and malicious firmware exploits. Through mobile-first engagement, users exploring device security now encounter Battlefield 6 as a key differentiator in trusted computing. **How Secure Boot Battlefield 6 Actually Works**
**Common Questions About Secure Boot Battlefield 6** ***Does it prevent all software-based attacks?** While not a complete shield against all threats, Secure Boot Battlefield 6 dramatically reduces the risk of unauthorized code execution, creating a far harder layer for attackers to bypass. ***Is it difficult to enable or update on my device?** Typically, implementation is handled through manufacturer or firmware updates. When properly integrated, it functions transparently, requiring minimal user interference. ***Does it affect device performance?** Security enhancements in Battlefield 6 are designed with efficiency in mind. Benchmarking shows only negligible overhead on startup and runtime operations. ***Can it be applied across different device types?** Yes, the framework supports a broad range of platforms—from mobile devices to embedded systems—adapting validation rules to device-specific use cases. **Opportunities and Realistic Considerations** Adopting Secure Boot Battlefield 6 presents clear advantages: stronger defense against supply chain compromises, improved compliance with data protection standards, and long-term confidence in hardware integrity. However, users should remain aware that no system offers 100% security. Compatibility with legacy components and update demands from vendors may influence adoption timelines. As the technology evolves, transparency about configuration, support ecosystems, and ongoing maintenance remains essential. **Misunderstood Aspects of Secure Boot Battlefield 6** A frequent concern is that secure boot restricts user control or customization. In reality, Battlefield 6 maintains user flexibility while safeguarding critical startup layers. Another myth is that it automatically fixes all system vulnerabilities—while it strengthens boot security, it works best when integrated with broader cybersecurity practices. By addressing these misconceptions, users gain a clearer understanding of how the technology supports, rather than limits, safe digital engagement. **Who Secure Boot Battlefield 6 May Be Relevant For** Businesses managing large fleets of devices benefit from its scalable, centralized firmware validation. Individual users gain peace of mind knowing their devices resist stealthy attacks from day one. Educators and researchers explore its integration in learning environments, while policymakers and device manufacturers rely on it as a foundation for secure-by-design product development. The framework’s adaptability makes it valuable across contexts. **Building Awareness Through Curious Exploration** Understanding Secure Boot Battlefield 6 invites readers to look deeper into secure computing practices beyond headlines. It encourages mindful engagement with emerging technologies that safeguard digital trust and device integrity. As awareness grows through trusted sources and real-world use, confidence in these systems strengthens across households and enterprises alike. Secure Boot Battlefield 6 isn’t just a technical update—it’s a shift toward greater resilience in an increasingly connected world. By prioritizing transparency, accuracy, and user education, this evolving standard reinforces the foundation of safe, stable digital environments for everyone.
Businesses managing large fleets of devices benefit from its scalable, centralized firmware validation. Individual users gain peace of mind knowing their devices resist stealthy attacks from day one. Educators and researchers explore its integration in learning environments, while policymakers and device manufacturers rely on it as a foundation for secure-by-design product development. The framework’s adaptability makes it valuable across contexts. **Building Awareness Through Curious Exploration** Understanding Secure Boot Battlefield 6 invites readers to look deeper into secure computing practices beyond headlines. It encourages mindful engagement with emerging technologies that safeguard digital trust and device integrity. As awareness grows through trusted sources and real-world use, confidence in these systems strengthens across households and enterprises alike. Secure Boot Battlefield 6 isn’t just a technical update—it’s a shift toward greater resilience in an increasingly connected world. By prioritizing transparency, accuracy, and user education, this evolving standard reinforces the foundation of safe, stable digital environments for everyone.
The Shocking Truth About Ztrip’s Forbidden Path You Need to See Now
Unlock Stardom Overnight With The Alphabet Code You’ve Never Noticed
This Simple Trick Will Crash WVUMYCHART’s Reputation Overnight!